Cyberattacks are on the rise—and they’re not just coming from one direction. According to recent news reports, phone calls claiming to be from the IRS are targeting elderly people. The caller states that money is owed and has to be paid by the end of the day, followed by personal questions intended to ferret out further identifying information. And since the callers already have names and numbers, many people fall victim to this approach.
Calls about infected PCs that mirror recent ransomware attempts are also on the rise. These claim to originate from local cable companies, stating that they have observed your computer is compromised and could be transmitting further infections. The caller then asks to remote into the person on the other end of the line’s machine, and once they do they disable critical functions and ask for $319 to fix it. If you don’t pay, your PC will suffer—and if you do pay, then you just gave a thief your credit card information.
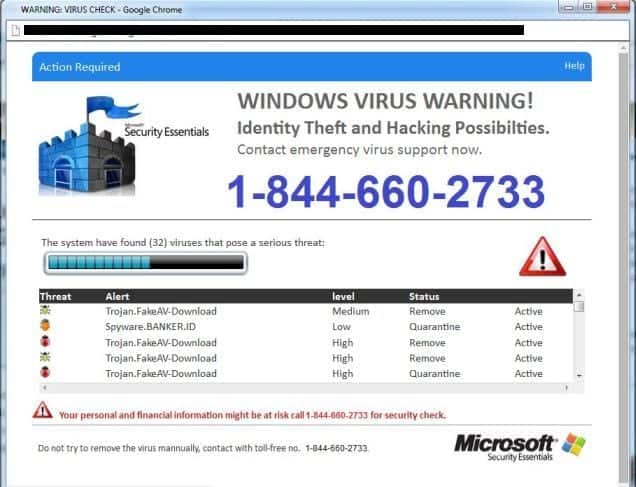
In the cyber realm, some computer users are reporting a pop-up window that warns them about their computer possibly being infected and requesting that they call Microsoft. This is a scam, but many people are falling for it.
If you see this screen or one like it (some people are reporting an FBI warning screen), close your Internet browser, unplug your computer from the network to prevent further infection, and call your trusted IT provider. Clicking anything on the pages that pop up might only make things worse.
Another scam that is growing in frequency is what is commonly known as Business Email Compromise. Messages arrive that purport to include an invoice that needs to be reviewed, but the attachment actually contains a program that launches the latest CryptoLocker variant and locks all your files. Or, an email that appears to come from a CEO, CFO, or other company executives may request a wire transfer that needs to be executed ASAP.
The only way to avoid this is to carefully look at the email address that sent the message—often, recipients will see their boss’ actual name in the Sender field, even though that’s just a label and the actual email address came from a Gmail or other free account. In addition, make sure you carefully vet each attachment before opening it. If you aren’t expecting an attachment from a specific person, don’t open it!
A dramatic increase in the number of phishing attacks that target an employee’s W-2 information has also occurred. These fake emails again look as if they’re arriving from a company’s senior executive requesting W2 information for all active employees. Collecting this information then allows thieves to commit tax fraud by filing fraudulent returns in order to receive refunds.
In CMIT’s experience, sometimes even the best spam filters will not prevent all of these emails from getting through. Consider these tips to keep your business, your employees, and your systems safe:
Five Tips to Protect Your Business from Cybercrime
1) Call to confirm before you respond. If you are asked to email sensitive information, always confirm with the recipient by calling them or inquiring in person—do not reply to the email.
2) If you aren’t sure, don’t click. Never click on links or attachments in emails unless you are absolutely positive about who the sender is, where the link directs, and what is in the attachment.
3) When you know it’s spam, do not respond. If you are spammed, do not write back and yell, curse, or tell them that you know it’s a fraud. You will gain nothing, and in some cases, you will cause yourself more harm because responding only confirms to the spammer that you and your email address are real.
4) Document suspicious emails and contact IT support. If you suspect an email or phone call to be a phishing attempt, document the number or address it arrived from and immediately contact IT support.
5) Report scams to authorities. You can also report email scams and phone scams to the FTC, IRS, or FBI via their websites.
The bottom line? Think before you click, stay alert, implement multiple layers of security on your PC and network, and never share any personal information with anyone who calls or emails you.
If you’re concerned about the safety and security of your business, your employees, and your systems, contact CMIT Solutions today to find out more.